Authentication: Password, Social, OIDC, and one-time access link
User authentication is a critical component of any online service. It involves verifying a user’s identity before granting access to certain features, services, or content. Ensuring secure, seamless, and user-friendly access to your platform can significantly enhance user engagement and satisfaction.
Authentication not only safeguards user accounts and personal information but also ensures seamless access to exclusive content, personalized user experiences, and efficient subscription management.
Arc XP Identity provides robust and flexible authentication solutions, including traditional email and password methods, integration with Google, Facebook, and/or Apple, and other third-party authentication providers under the OpenID Connect (OIDC) protocol for a more unified user experience. These solutions are designed to meet the diverse needs of end users.
This section guides you through the authentication options supported by Arc XP Identity. Additionally, we explore the use of one-time access links, a convenient option that bypasses the need for permanent credentials, or enables the end user to access their account temporarily when they do not remember their password, offering a secure and user-friendly authentication process.
Regardless of the authentication type, Arc XP Identity uses JSON Web Tokens (JWTs) for tracking a user’s calls to protected public APIs. Each time a user is successfully authenticated into the system, two JWTs are assigned:
-
access-token: a limited lifetime token that tells us who the user is (15 minutes by default)
-
refresh-token: a token that you can use to obtain a new access token when the old one expires. You can customize the lifetime for the refresh-token in the CSR tool.
When you use a valid access token, the system recognizes the user as logged in, and the user can access the privileges assigned to their account.
Options exist to incorporate these flows into your website using PageBuilder Themes blocks. You can further enhance PageBuilder blocks by developing custom flows. Additionally, you have the flexibility to tailor these to your specific requirements by leveraging our SDK methods and APIs.
The JWTs that Identity produces are signed according to the HS256 protocol (Hash-based Message Authentication Code), an algorithm that takes the payload to be signed and a secret and applies a crypto algorithm to produce the signature.
Features and workflows
Third-party authentication providers
To make the end-user experience as smooth and secure as possible, we offer easy sign-in options using popular third-party authentication providers: Google, Facebook, Apple, and third-party auth providers under the OIDC protocol. When a user logs in with one of these services, Arc XP Identity automatically creates a new account.
This authentication mechanism offers several advantages:
- Users do not need to remember additional passwords.
- If the tenant (organization + site) has enabled email verification, users signed in through social providers do not require email verification.
When a user attempts to log in using a third-party authentication provider, the system prompts them to sign in to that provider and grant your site access to their basic profile information. When the user authenticates, the provider returns an authorization code or token (along with additional information if you are using the OIDC protocol). The system then uses this data to request user information from the provider, authenticate the user on your site, and create or update the user account as needed.
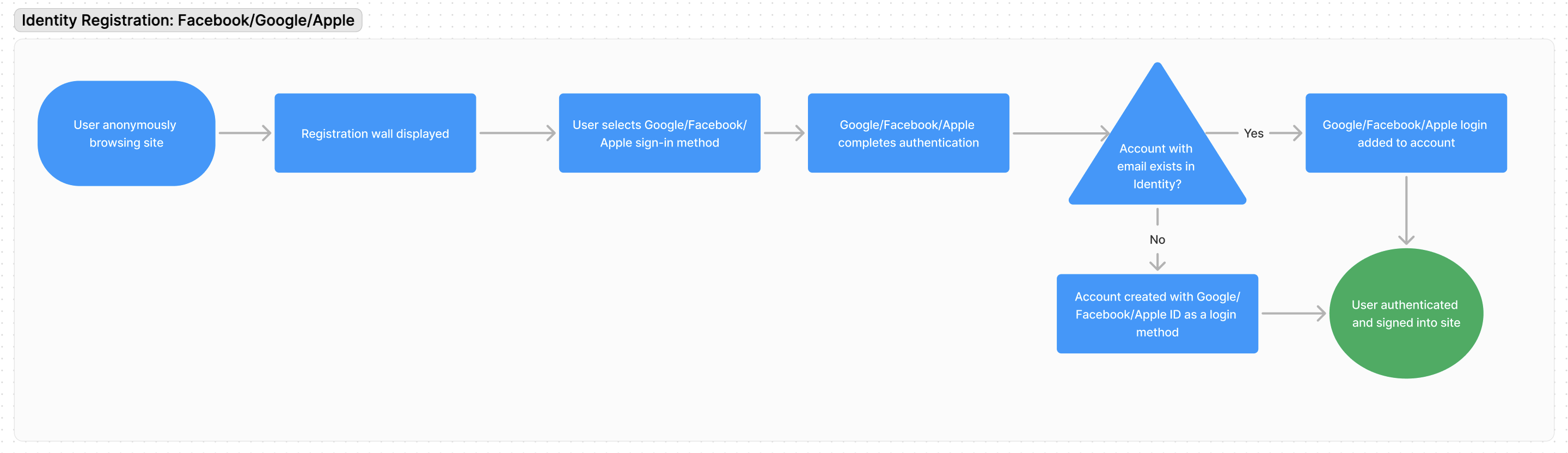
Authentication with third-party authentication providers: Facebook, Google and Apple
Arc XP Identity offers integration with some of the most popular third-party authentication providers: Google, Facebook, and Apple.
See Configure Third-party authentication providers, Facebook, Google, and Apple for additional details.
Authentication OIDC
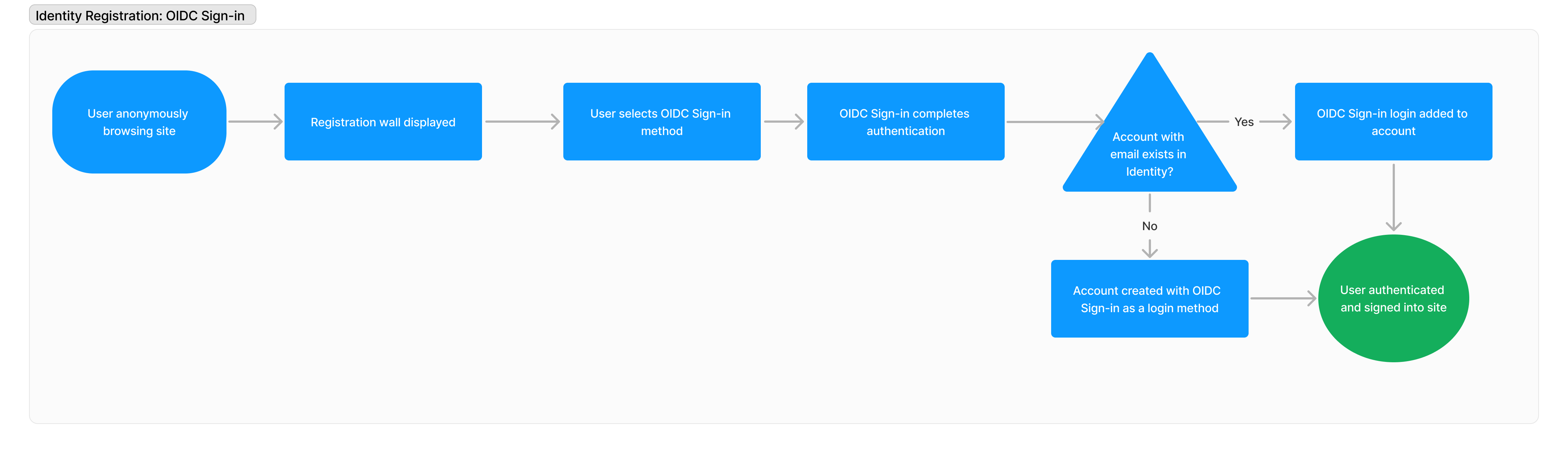
Given the extensive range of sign-in options available worldwide, which varies by region, service provider, and platform, Arc XP Subscriptions supports OIDC integration. This integration enables your customers to use any of their social profiles to connect to your site when you build a sign-in flow over the OIDC protocol. You can also use this integration with other IDPs like Auth0 as long as they are using the OIDC protocol.
Authentication with email and password
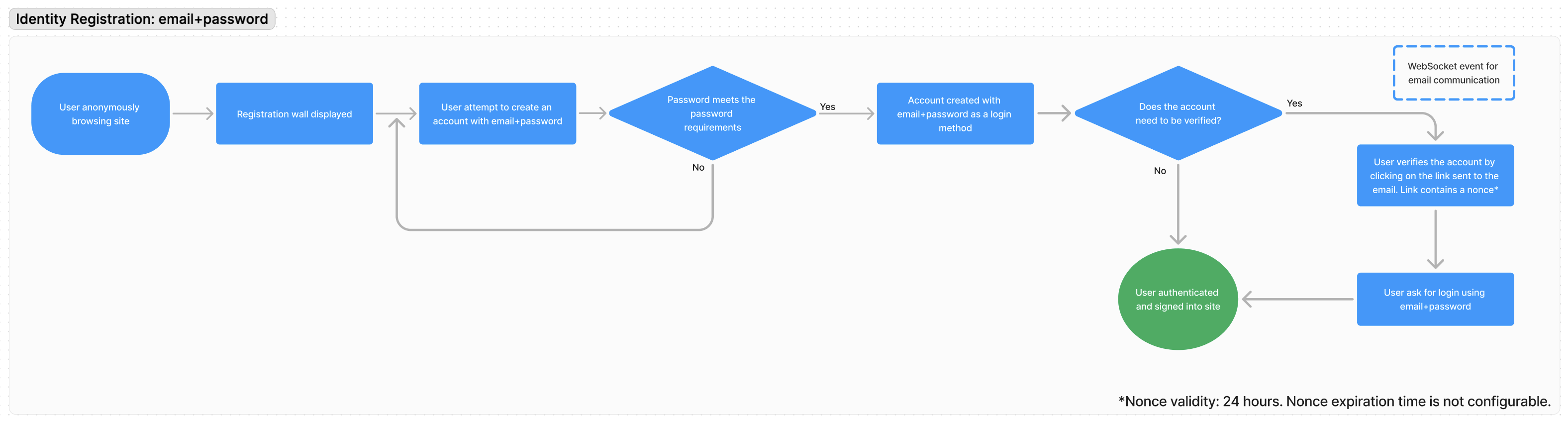
During the sign-up process, users are able to use the traditional email-and-password method. However, Arc XP Identity offers some customizable features that are involved as part of this process:
- Password requirements: User accounts are created only if the password meets the system-defined requirements. For example, you might require the password to be at least eight characters long, include both uppercase and lowercase letters, contain at least one numerical digit, and include at least one special character (such as
!,@,#, or$). Failure to meet these criteria prevents the system from creating the account. You can set up these requirements in the Admin tool. - Enforce email verification: Enforcing email verification is an optional feature that you can enable to prevent spam or junk user accounts from accessing the system. When a user attempts to sign up, a verification email is sent. The user must click the link in this email to verify their account. After verification, the user can to log in to the system. You can enable or disable this setting in the Admin tool.
One-time access link for password-less sign-in
For those users who already have an account but do not remember their password, users can request a one-time access link be sent to their email address rather than reseting their password. This will generate a WebSocket event that with a nonce clients can send using their email service provider for clients to authenticate. For security purposes at this time, this token expires after 24 hours.
Limitations
refresh-tokenexpires every 24 hours
Account unification
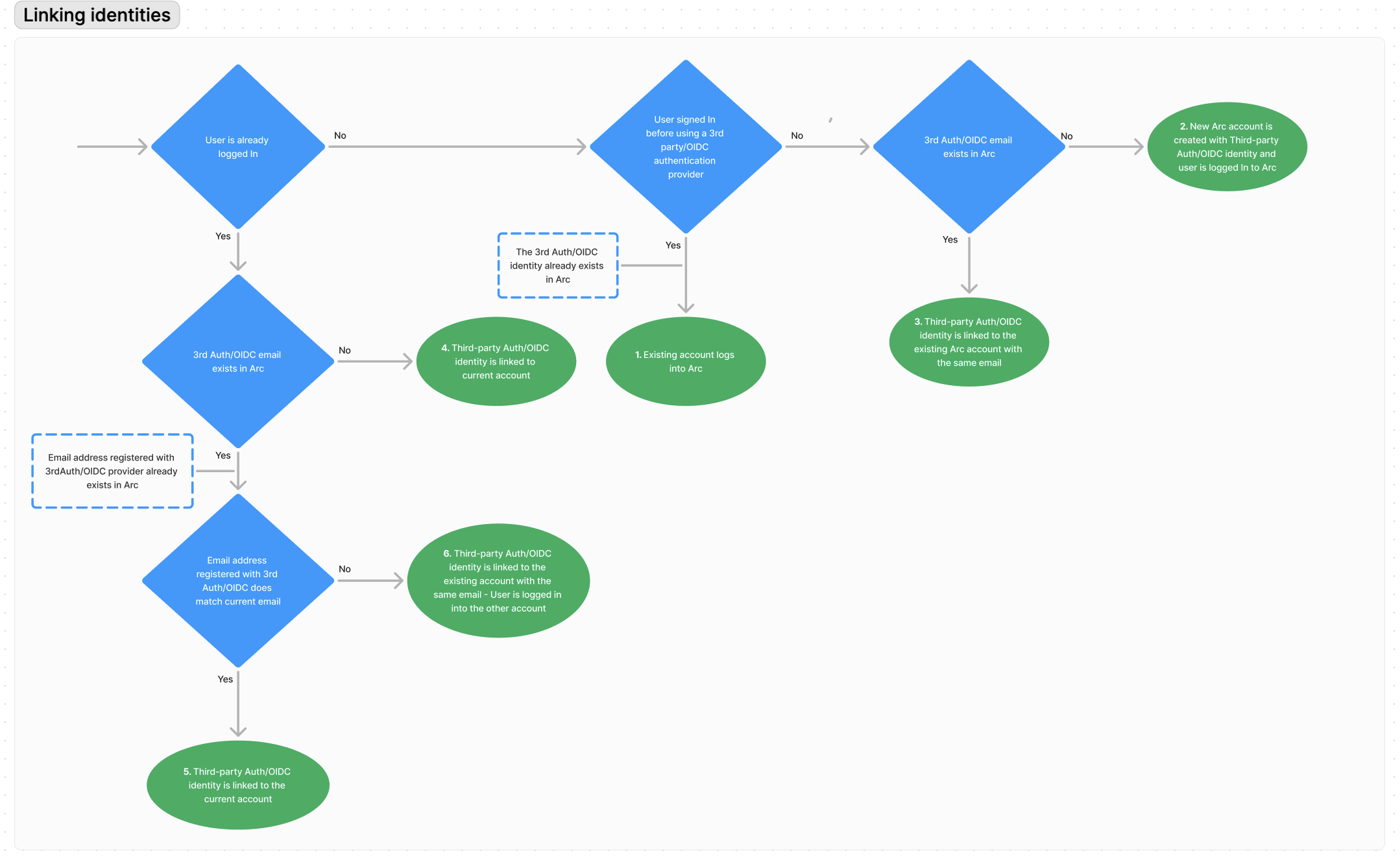
Multiple authentication identities, one account
With the rise of various social providers, it’s common for the same email address to be used for accounts across various platforms like Facebook, Apple, Kakao, and others. For example, users can create an Apple account with a Gmail address. While Apple provides its own authentication method, which requires you to set up new credentials, users can still use a Gmail address to verify and identify their identity.
As part of the authentication process with third-party providers, end users grant your site access to basic profile information from the external provider. Arc XP Identity uses this email to create the user account within the system. Each account on Arc XP Identity has a unique, primary email, which either the user provides (for example, email and password) or the third-party provider provides.
Because each account has a unique, primary email, if a user attempts to authenticate using accounts from various third-party providers, Arc XP Identity uses account unification. Account unification connects all social logins and email accounts into one account, regardless of the authentication type—Facebook, Google, Apple, or OIDC. Each third-party provider creates a new identity that is attached to the existing user account.
In fact, depending on whether the end user is logged in or not and the email profile information provided by the third-party provider, Arc XP Identity behaves differently—either creating a new account or attaching identities to an existing user account.
The following table and diagram explain the various scenarios.
| Scenario | Conditions | Results |
|---|---|---|
| 1 |
|
|
| 2 |
|
|
| 3 |
|
|
| 4 |
|
|
| 5 |
|
|
| 6 |
|
|
In the table, the phrase ‘third-party account’ refers to the integrations that Arc XP Identity supports with Google, Facebook, Apple, or any other third-party provider under the OIDC protocol.
Single Sign-in (SSO) with Arc XP Identity
-
Identity is an OIDC provider; therefore, you can use Identity as a provider for authentication on external sites to create a single sign-on experience.
-
Arc user accounts can be used to authenticate on your other sites or services
Recommended practices and uses
-
Use social sign-in before email and password. Implementing social sign-in options allows users to create accounts without needing to remember an additional password. This improves user experience and reduces friction of having to enter, and remember, a password.
-
Set username to equal email for sign-in. Configure usernames to be the same as email addresses. This configuration should be requested during tenant onboarding. We strongly recommend this approach because both the username and email are unique, which helps avoid potential issues with user account updates.
-
Verify email before allowing access. Ensure that users verify their email addresses before granting access. Refer to the security documentation for more details.
-
Prefer SDK methods over APIs. Use our SDK methods rather than direct API calls when possible. The SDK handles JWT token refreshing, manages public requests, and ensures the JWT is passed with each request as needed. Additionally, the SDK offers options to share the same user session across different tabs (for example, using the rememberMe option)).-

