Secure your site against attacks: CORS Domains, Blocked email domains and reCAPTCHA
Arc XP Subscriptions provides you several tools that helps you protect your site. It is the client’s responsibility to configure and use these tools according to their needs.
CORS Domains
Cross-Origin Resource Sharing CORS is an HTTP-header based mechanism that allows a server to indicate any origin from which a browser should permit loading resources. In Arc XP Subscription, you can easily configure allowed CORS domains via the Admin tool. This setup allows customers to protect their site by limiting access to public APIs.
The CORS functionality is backward compatible, meaning that you do not have to do anything immediately as it will honor what origin sends. At your leisure, you can add valid origins to test the functionality. Once origins are added after the first time, then the system will always ensure that it respects the configuration.
You can set up CORS domains via the Admin tool. By clicking on the Settings tab in the Security section of the sidebar, you will find the CORS Domains tab.
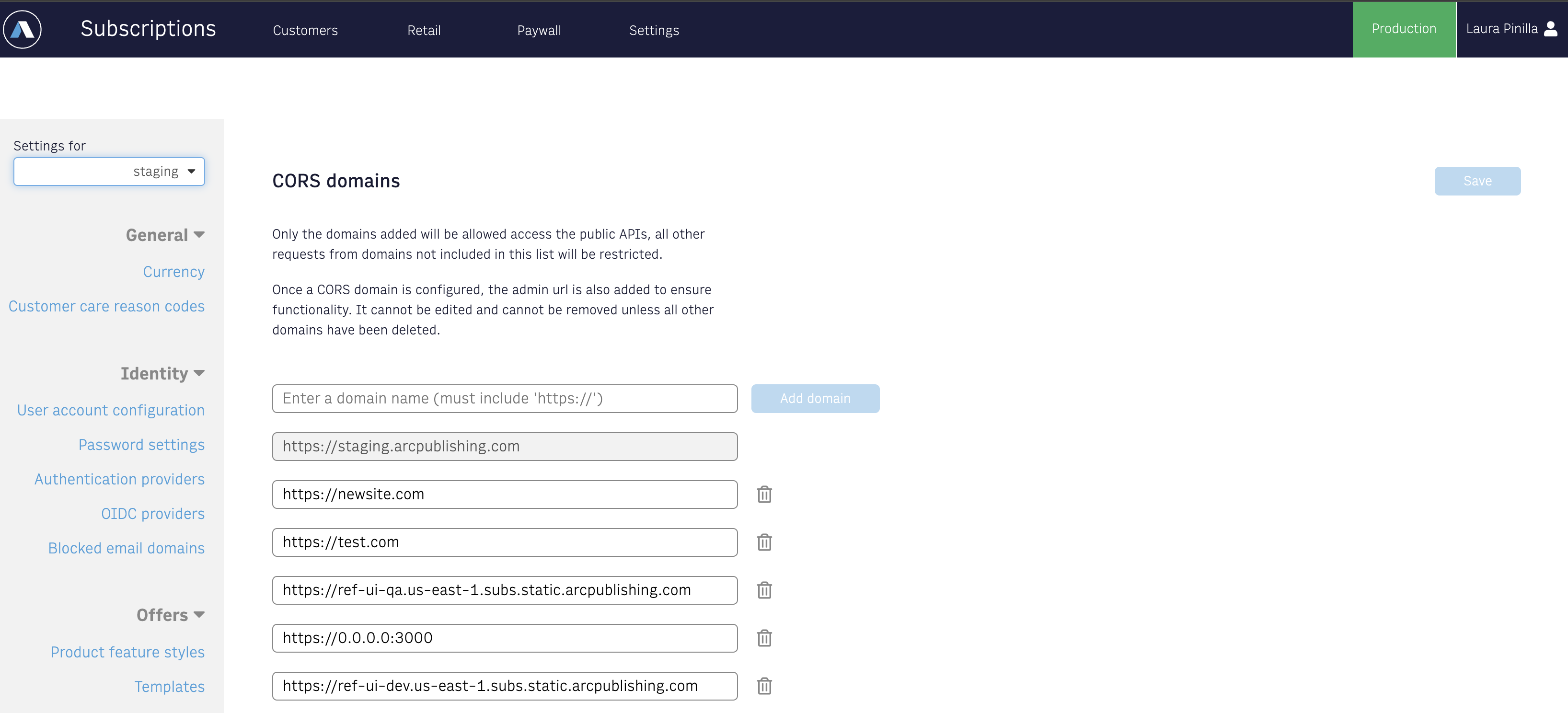
For the CORS domains, it can take up to 10 minutes for the updates to be reflected across all the APIs due to caching.
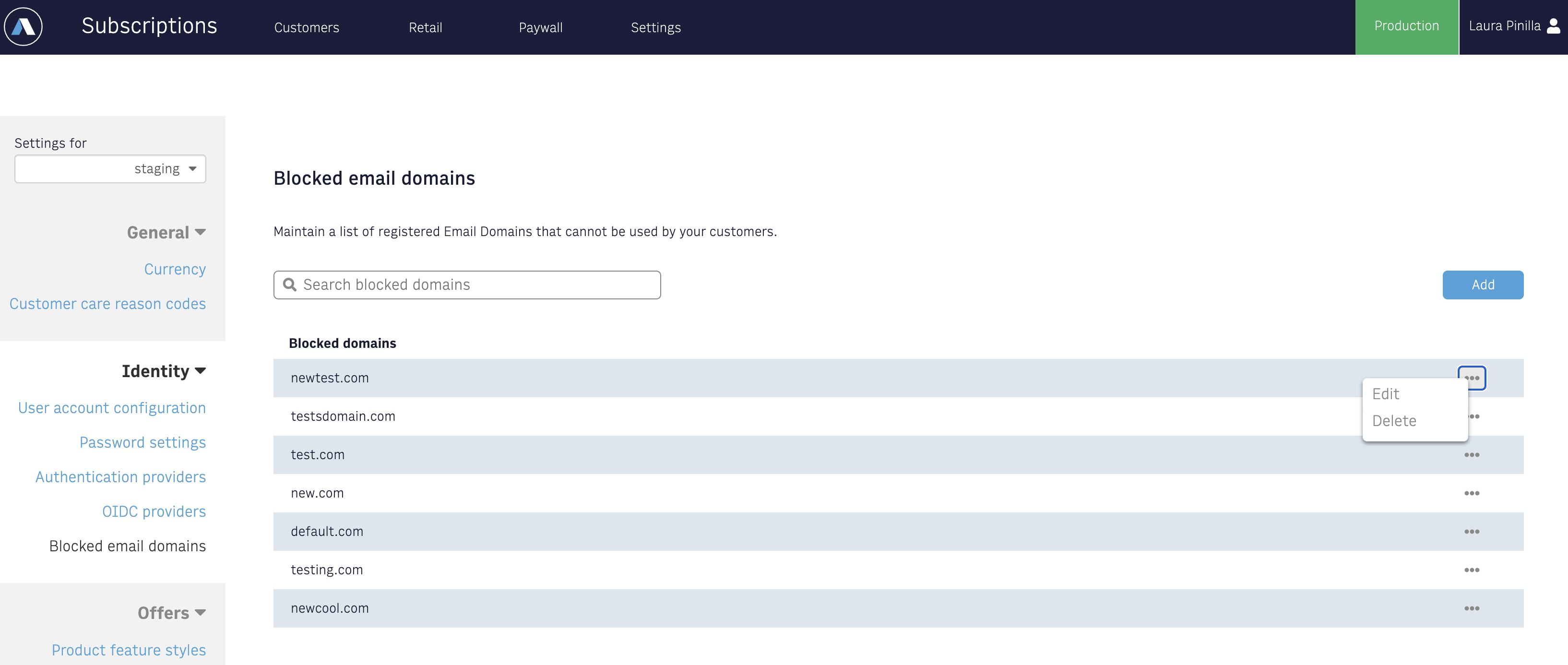
Blocked email domains
There are known bad actor email domains that can create a high volume of malicious requests, or ones that you can detect over time. These can be restricted by adding the domains to the Blocked Email Domains list in Settings.
reCAPTCHA
It is important to take steps to deter bots and other malicious actors from abusing your system. Arc XP subscriptions provides protection by using reCAPTCHA across different flows:
- User registration
- User Sign In
- One-time access link
- Checkout
You can set up and enable this protection for some or all these flows.
reCAPTCHA is a sophisticated type of CAPTCHA** developed by Google that helps differentiate between human users and bots. Google provides different versions of reCAPTCHA, including reCAPTCHA v2, which presents challenges to users, and reCAPTCHA v3, which assesses user interactions in the background to detect suspicious behavior. Arc XP Subscriptions supports integration with both: reCAPTCHA v2 & reCAPTCHA v3. You should use the same version for all the flows in which you decide to enable the feature. But, you can use different versions for each tenant (organization + site)
| VERSION | reCAPTCHA V2 | reCAPTCHA V3 |
|---|---|---|
| Description |
|
|
| Pros | These challenges are designed to be simple for humans to solve but difficult for automated systems | Improves the user experience by eliminating the need to disrupt their browsing with reCAPTCHA challenges |
| Cons |
|
|
| What it looks like |   |  |
To have reCAPTCHA protecting your site, follow the next steps:
-
Create reCAPTCHA keys for websites (Google developer console)
- Go to The ReCAPTCHA Admin Site
- Register a new Site: choose the reCAPTCHA type, and domains allowed. Once the form is fulfilled Google reCAPTCHA Admin Site returns the Site Key and Secret Key.
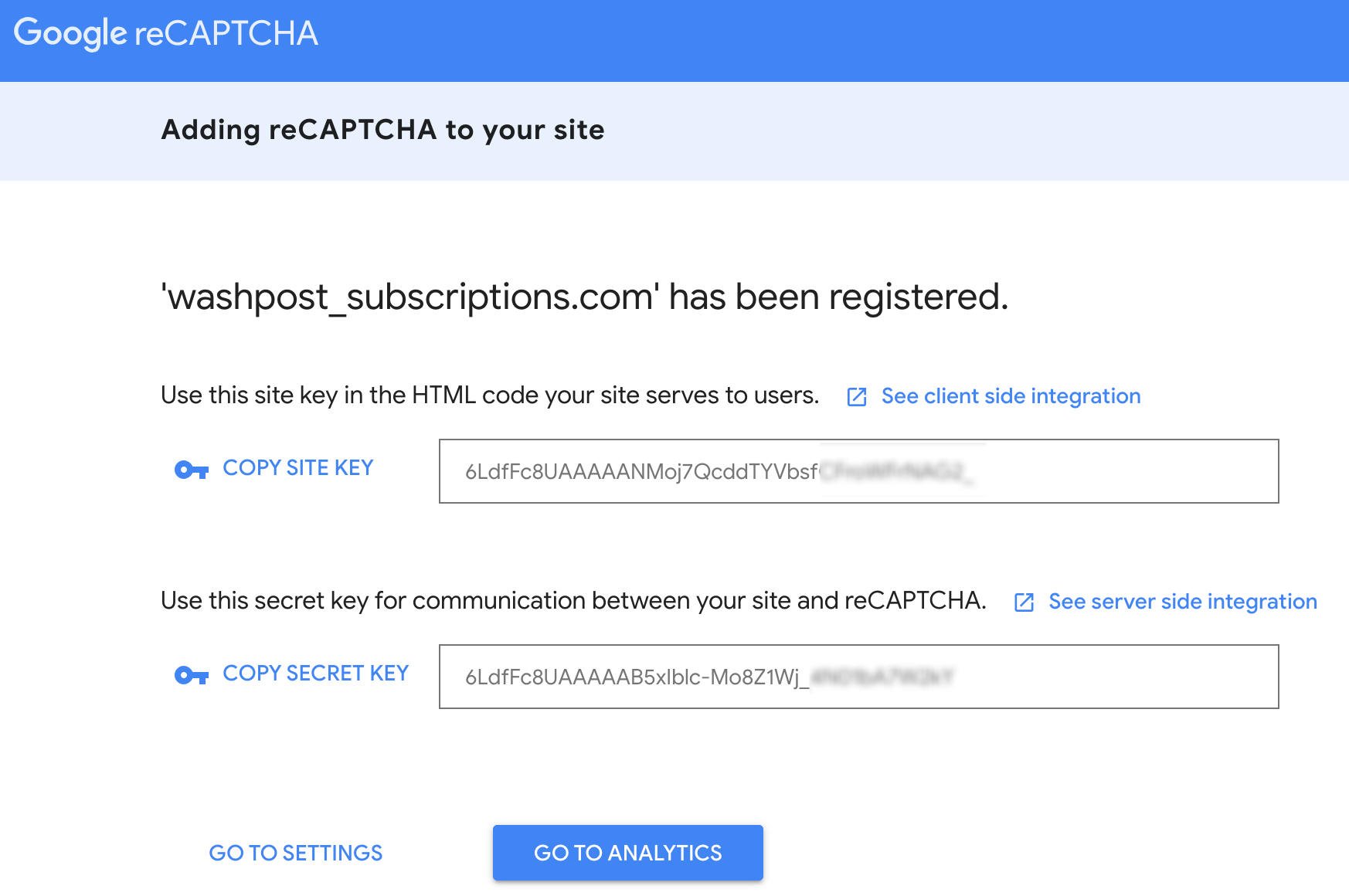
-
Configure reCaptcha on Admin tool Copy and paste Site Key & Secret Key from the Google reCAPTCHA console into the Admin tool under the Security tab. Recaptcha must be set up and enabled for each site where you want to protect your flows. If using reCAPTCHA v3, also enter your risk threshold percentage.
In addition to enter the reCaptcha settings, you will need to decide what are the flows you want to protect with reCAPTCHA.
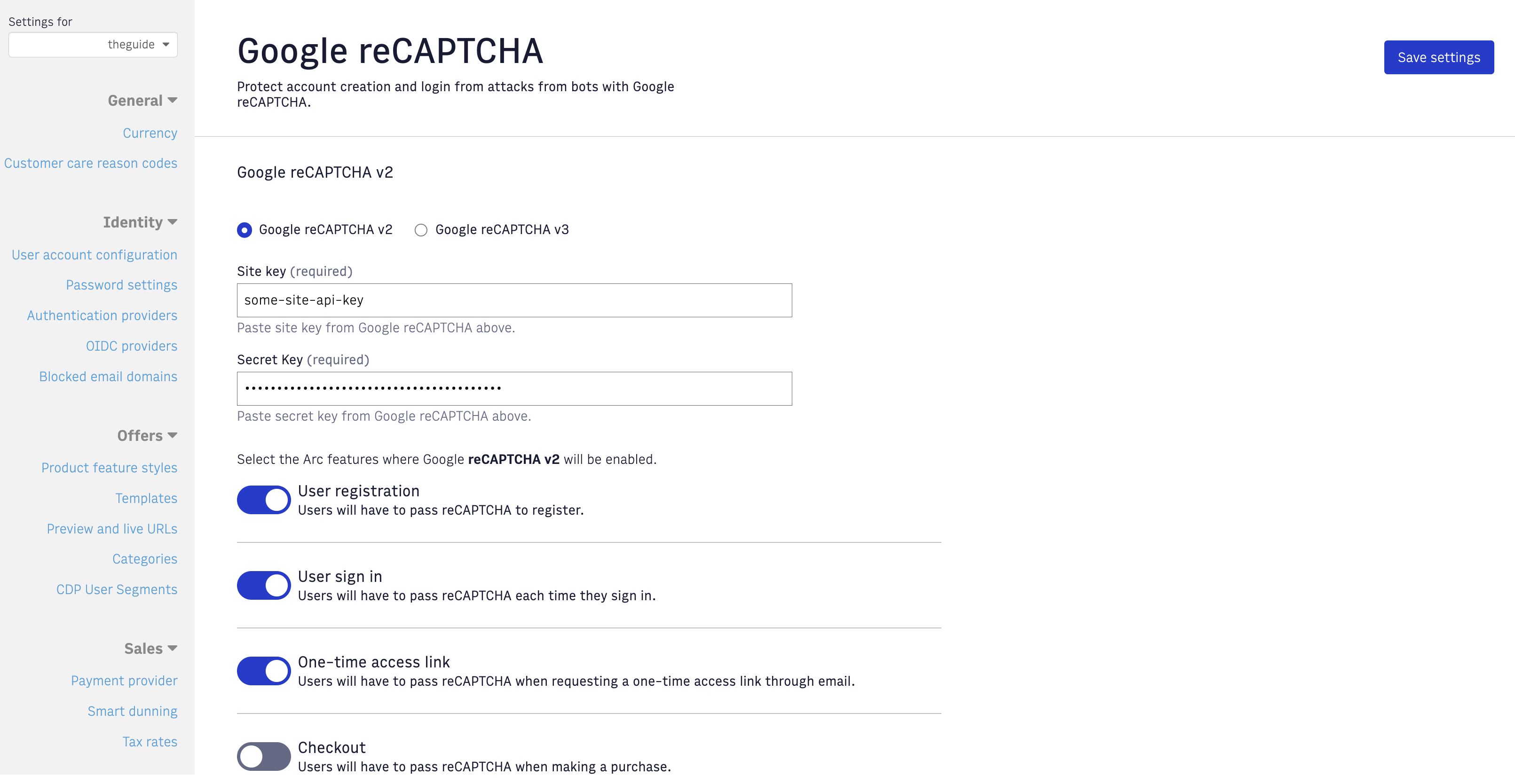
-
Include the reCAPTCHA widget on your page form.
The reCAPTCHA widget needs to be included as part of each page form where this feature was enabled. If you are using our Subscription blocks, you only need to include the block(s) on each page. When adding a block to a page, the system automatically checks the tenant’s settings. Based on whether reCAPTCHA has been set up and which flows it has been enabled for, the Google widget will be provided as part of the form.
The following blocks use reCAPTCHA:
- Identity Sign Up - Arc Block
- Identity Log In - Arc Block
- Identity One Time Password Request Form - Arc Block
- Subscriptions Checkout - Arc Block
If you want to implement this by your own, please see How-to: Implement Sign Up, Login and one-time-access link
Frameworks:
There are packages in npm that you can use to help you integrate reCAPTCHA into your UI easily. Below are a few examples for different frameworks.
- https://www.npmjs.com/package/react-google-recaptcha (React)
- https://www.npmjs.com/package/angular-google-recaptcha (Angular)
- https://www.npmjs.com/package/vue-grecaptcha (Vue)
Passing the reCAPTCHA token
If you do not use our SDKs, the token returned by Google’s SDK should be submitted to Arc in a top-level field, in the JSON body, named recaptchaToken. This same token can be used twice: first when creating an order and then again when finalizing the payment.
When using the SDK, all the same rules apply, but you must pass the recaptchaToken token to the SDK methods that require it. Currently, the seven methods that can accept a recaptchaToken token are:
SDK METHOD API Identity.login() GET /identity/public/v1/auth/loginIdentity.signUp() POST /identity/public/v1/signupIdentity.requestOTALink() POST identity/public/v1/auth/magiclinkIdentity.requestResetPassword() POST /identity/public/v1/password/resetSales.createOrder() POST /sales/public/v1/checkout/orderSales.finalizePayment() PUT /sales/public/v1/checkout/order/${orderNumber}/payment/${paymentMethodID}Sales.finalizePaymentUpdate() PUT /sales/public/v1/paymentmethod/${paymentID}/provider/${paymentMethodID}/finalize
**CAPTCHA (an acronym for “Completely Automated Public Turing Test to Tell Computers and Humans Apart”) is a security measure designed to differentiate bots from humans, typically with an image or audio challenge. CAPTCHAs are widely used on the internet to prevent bots from signing up for accounts, spamming comments, and buying products.

