Redirects API
This document aims at providing the user a deep dive into Redirect APIs to perform the following tasks. Read What are the different kinds of redirects in Arc XP? before accessing these APIs.
- Add a redirect rule
- Bulk upload multiple rules
- Edit an existing redirect rule
- Delete a redirect rule
- Activate the version
- Download an activated version as well as previously activated version
Prerequisites
- Working knowledge of HTTP and REST
- Working knowledge for creating JSON payload/file
- You need the
{site_id} - Use
cloudlet_typeasredirectorin the endpointapi.[orgId]
https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule?Accessing the Redirect APIs
If you don’t already have an All Access Arc XP developer token, navigate to Administration → Developer Center → Create Tokens and click Create All Access Token. You will be presented with a unique token for you to use as the Bearer token when accessing Edge Redirector APIs (details on how to implement will be provided when creating the token).
Refer to Accessing the Arc XP APIs for more information.
Swagger Document for APIs
See Arc XP Delivery API.
Using the API Endpoints
The following sections walk you through various operations you can perform via these APIs
Viewing the rules under the activated version or current working set
To view the rules:
Command to execute
curl -H "Authorization: Bearer " \-X GET "https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule?limit={}"Response
{ "rules": [ { "id": "d779d7a9-262f-4ad2-9df2-0db7b9bee85f", "status": "NEW", "siteId": "staging-qatesting-sandbox", "policyType": "redirector", "sort_key": 16425880019999900, "submittedBy": "ktran", "submittedAt": "1642588001", "ruleContent": { "end": 0, "matches": [ { "caseSensitive": false, "matchOperator": "equals", "matchType": "regex", "matchValue": "^https?://(?:[A-z0-9|\\.]*)/(.*)", "negate": false } ], "name": "d779d7a9-262f-4ad2-9df2-0db7b9bee85f", "redirectURL": "http://abc.com", "start": 0, "statusCode": 302, "type": "erMatchRule", "useIncomingQueryString": true, "useRelativeUrl": "none" }, "warning": "Regex value could potentially match more paths than possibly expected" } ]}Adding a single rule
Command to execute
# Payload{ "redirectURL": "http://test.com", "useRelativeUrl": "none", "matches": [ { "matchType": "regex", "matchValue": "^https?://(?:[A-z0-9|\\.]*)/(.*)", "matchOperator": "equals", "negate": false, "caseSensitive": false } ]}
# Commandcurl --request POST --header 'Authorization: Bearer ' --url https://[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/ruleResponse
HTTP 201 OKAdding multiple rules
Details regarding payload CSV format
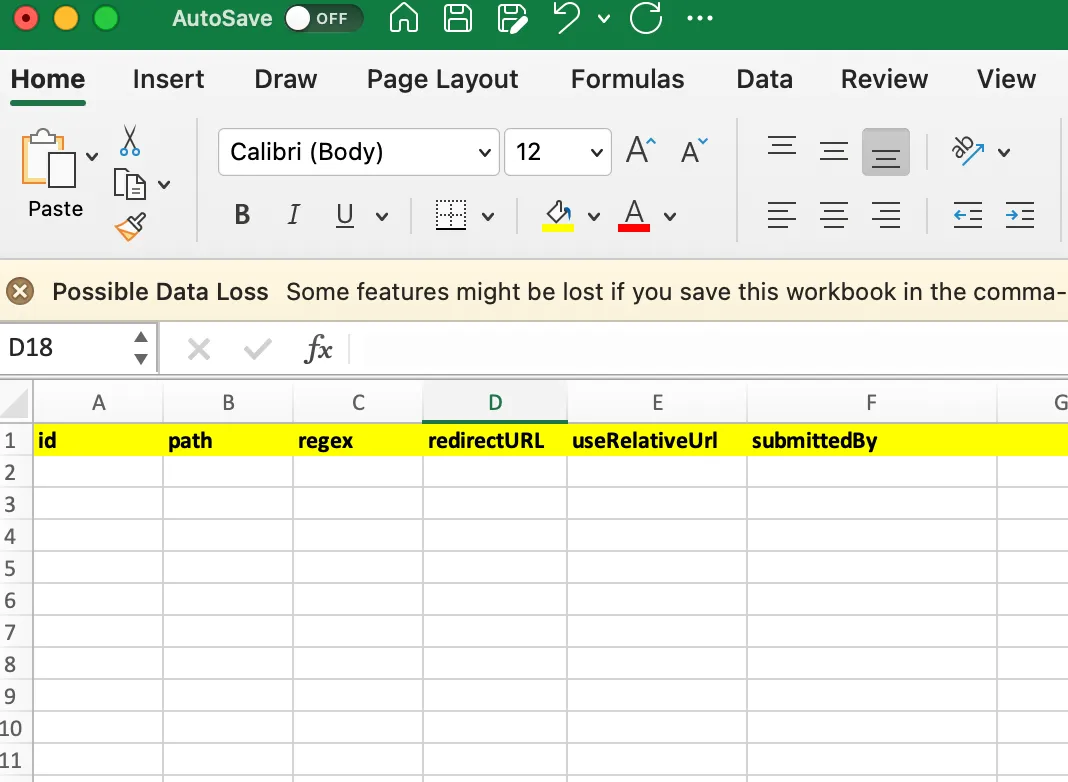
Command to execute
curl --request POST \ --header "Authorization: Bearer " \ --url https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule-csv \Response
{ "task_id": "fa03a4c6087940e485a6c03b6a4e9f76", "warning": ""}Updating an existing single rule
Command to execute
# Payload { "redirectURL": "http://testRulesUpdate.com", "useRelativeUrl": "none", "matches": [ { "matchType": "path", "matchValue": "/products/wildcards/*.jpg", "matchOperator": "contains", "negate": false, "caseSensitive": false }, { "matchType": "path", "matchValue": "/products/literals/*.jpg", "matchOperator": "equals", "negate": false, "caseSensitive": false }, { "caseSensitive": false, "matchOperator": "equals", "matchType": "regex", "matchValue": "something.*", "negate": false } ]}# Commandcurl --request PUT --header "Authorization: Bearer " --url https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule/Response
HTTP Response 200 OKModifying multiple rules
Command to execute
# PayloadCSV file to be attached
# Commandcurl --location --request PUT 'https://dev-api-usea1.customer.origin.aws.arc.pub/delivery-api/v1/cloudlet/redirector/site/staging-qatesting-sandbox/rule-csv' \--header 'arc-organization: staging' \--header 'arc-environment: sandbox' \--header 'arc-v2-username: ' \--header 'arc-service: user' \--form 'file=@""'Response
202 successful responseDeleting a rule
Command to be executed
- Get the rule_id
- Delete the rule
Get the rule
curl --request GET \ --header "Authorization: Bearer " \ --url https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule/Delete the rule
curl --request PUT \ --header "Authorization: Bearer " \ --url https://api.[orgId].arcpublishing.com/delivery-api/v1/cloudlet/redirector/site/{org-site-env}/rule/{rid}/Response
HTTP Response 201{ "success": true}Activating the policy
Command to be executed
curl --location -g --request POST 'http://{{host}}/delivery-api/v1/cloudlet/redirector/site/staging-ktran1-sandbox/version/' \--header 'arc-organization: staging' \--header 'arc-environment: sandbox' \--header 'arc-v2-username: ascac' \--header 'arc-service: user'Response
HTTP 200{ "task_id": "string", "warning": "string"}Unlocking the version
Use the command in case of the functionality is locked for quite some time because of activation or some other backend error
Command to be executed
curl --location --request POST 'https://dev-api-usea1.customer.origin.aws.arc.pub/delivery-api/v1/cloudlet/redirector/site/staging-qatesting-sandbox/unlock' \--header 'arc-organization: ' \--header 'arc-environment: ' \--header 'arc-v2-username: ' \--header 'arc-service: userResponse
HTTP Response 200 OK
